Security
- Passwords: not easy to guess or crack; No default or blank paswords; change periodically?
passwordsgenerator.net
Brute-force the hashed passwd file.
Default passwords
- Firewalls: host-based or network-based, ACL packet-filtering by IP or port,
stateful inspection, (caching) proxy server. NGFW (next generation)/ Layer 7 / UTM (unified threat mgt.):
understand application.
- Antivirus, malware (virus, trojan horse, ransomware, rootkit, keylogger, spyware, botnet etc. )
Updated with virus signatures.
- Install and running minimum services.
- Least privilege. RBAC (role-based access control). Zero-trust (verify everything).
- Updates/patches, esp. security fixes ("hot fixes")
- Backups of data. LTO tape cartridge 18TB (2018). Robotic tape library 180 PB. Offsite is ideal.
- Log files enabled and review. syslog. SNMP. NetFlow
- Disaster recovery. Business continuity.
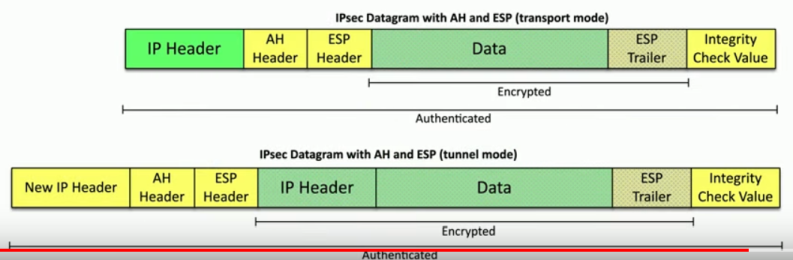
- Security protocols: IPSec (AH and ESP), PPTP, L2TP, SSL/TLS, SSH, VPN, WEP/WPA/WPA2/WPA3
- User training/education, procedures, policies, punishments.
On-boarding. AUP (acceptable use policy).
NDA (non-disclosure agreement).
- AAA: authentication, authorization, accounting. RADIUS, TACACS+, Kerberos (SSO: single sign-on ticket)
- Physical security: gates, guards, guns, locks, badges, biometrics, cameras, asset tags,
mantrap/airlock/vestibule to prevent tailgating or piggybacking. Dumpster diving.
Shoulder surfing. Privacy filter on screen.
- Confidentiality (secret) and authentication.
- Recovery: cold, warm, hot, cloud sites.
MTTR: mean time to repair; MTBF: mean time between failures
- Redundancy / High Availability: active-passive, active-active, diverse paths;
FHRP (first hop redundancy protocol);
VRRP: virtual router redundancy protocol)
- AIC: availability, integrity (unchanged: hash is message digest; digital signature is encrypted hash: 'I' made it),
confidentiality (private/secret: encryption, access control)
- Vulnerability assessment, scan. Penetration testing. Posture assessment.
Risk assessment.
-
SIEM (security information and event management): logs, trends, alerts; forensic analysis
- Rogue DHCP server, WAP; wireless evil twin
- PDoS (permanent), MITM (man in the middle), BYOD (bring your own device),
DLP (data los prevention), SLA (service level agreement)
- DMZ/screened subnet: publicly-accessible services separate from internal network