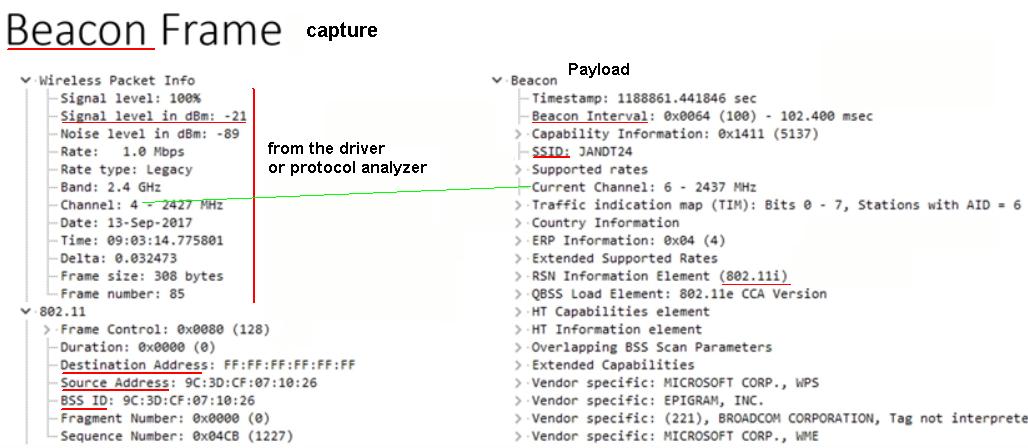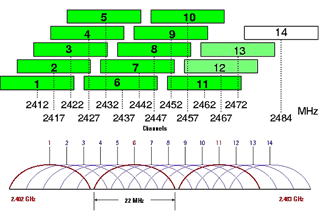
Channels 1, 6 and 11 are "non-overlapping" (or do channels have to differ by five or more, e.g. channels 2 and 7 non-overlapping?)
802.11 WiFi WLANs
| IEEE | 802.11b | 802.11a | 802.11g | 802.11n | 802.11ac "WiFi 5" |
802.11ax "WiFi 6" |
|---|---|---|---|---|---|---|
| Year | 1999 | 1999 | 2003 | 2009 | 2014 | 2018-21 |
| Frequency Band | 2.4 GHz (ISM) | 5 GHz (U-NII) | 2.4 GHz (ISM) | 2.4 and/or 5 | 5 GHz | 2.4&5 GHz 6 GHz: Wi-Fi 6E |
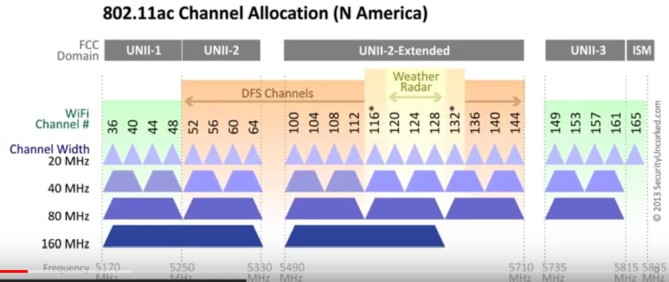
| # Channels (#non-overlapping) | 11 (3) @22MHz | 23 (12) @20MHz | 11 (3) @20MHz | (24) @20MHz / @40MHz | (24) 20,40,80,160,80+80 | ? 20,40,80,160,80+80 |
| Max theoretical speed (Mbps) | 11 | 54 | 54 | 600 (4@150M) | 6.8Gbps (8@867M) | 9.6Gbps (8@1.2G) |
| Speeds req'd (Mbps) | 1,2,5.5,11 | 6,12,24 | 6,12,24 | many | ||
| Optional Speeds (Mbps) | 9, 18, 36, 48 | 9, 18, 36, 48 | many | |||
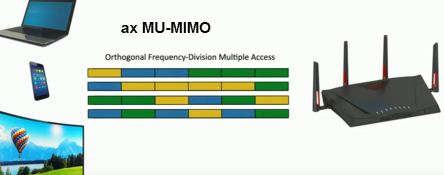
| Encoding/Modulation | DSSS (semicircular | OFDM (squared-off | DSSS (11Mbps) / OFDM (54Mbps) | OFDM MIMO / SDM, beamforming (1 device) | 8 DL MU-MIMO multi-user. beamforming (4 devices) | OFDMA. 8 bi-directional (DL and UL) MU-MIMO |
| notes | Block-ACK. MIMO: multiple antennas. Up to 4 streams @40MHz. frame aggregation. larger range. | up to 8 streams @160MHz to separate devices. channel bonding |
(antennas on AP) x (antennas on client) : streams
2x2:2, 3:3:2, 4x4:4
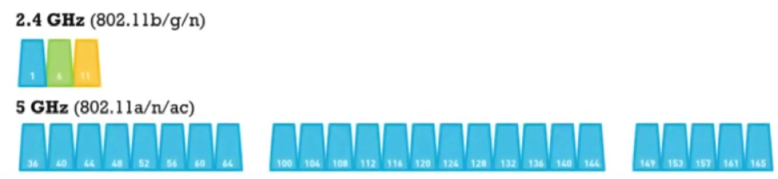
2.4 Channels: USA: 11; Europe: 13, Japan 14.
Weaker signals data-rate-shift down to lower speeds. transmission by transmission, per client (per frame?)
Higher frequency-->faster but smaller coverage.
Any b WNIC in a g network causes all transmission to drop down to b speeds.
WAP of g network can disable b mode: "Protection".
Any g WNIC in a n network causes all transmission to drop down to g speeds.
WAP of n network can disable b/g mode.
Can upgrade laptop to USB 3 radio with external antenna
(avoid the tiny ones, lack of heat sink limits lifetime).
Upgrade desktop with WNIC with external antennae.
Matter absorbs, reflects, scatters signal. MIMO likes multipath interference?
Radio propagation is complex:
sporadic and usually temporary losses due to fading, shadowing, hand off.
Interference from overlapping channels, other machines (Bluetooth, cordless phones, microwave ovens,
baby monitors, motion detectors, fluorescent lighting, RFID reader, radar, drones etc.).
2.4GHz band (slightly) longer range than 5GHz band.
b/g: 2.400-2.487GHz. Channels 20/22 MHz wide every 5 MHz
a: 5GHz
n: channel either 20 or 40 MHZ wide (if 40, then only one nonoverlapping in 2.4GHZ band)

Channels 1, 6 and 11 are "non-overlapping"
(or do channels have to differ by five or more, e.g. channels 2 and 7 non-overlapping?)


WLAN [W]AP WNIC
WAP like a shared Ethernet hub (half-duplex and only one transmitter at a time): CSMA/CA
transmitter can't simultaneously receive, so no collision detection (CD) possible,
thus CA with explicit ACKs.
WAP: bridge to cabled network.
Nodes/stations:
receiver: if no bit errors (i.e. does a checksum) then send ACK frame immediately.
sender: if don't get ACK then assume failure and resend
optional (configurable in WAP): RTS/CTS (Request To Send / Clear To Send) frames exchange between nodes to solve "hidden node" problem.
Modes:
ad hoc (Independent BSS [basic service set]). No WAP.
Stations transmit directly to [all] other stations. No connectivity to other networks.
infrastructure: all communication via WAP. and to connect to LAN. BSS/cell
ESS [extended service set]: multiple WAPs (different channels) for roaming (with same IP address)
client/station associates with AP.
SSID 32 ASCII character: same for all APs of ESS.
broadcast by AP in periodic beacon (100 ms) or turned off,
appears as "unknown network" or nothing depending on client.
AP can have multiple SSIDs (each a different MAC) but still one channel.
APs on same channel can work (slowed). APs on overlapping channels will interfere
because frames are not clearly received.
Can be multiple SSIDs for each radio, each corresponding to different network,
e.g. Guest vs /internal.
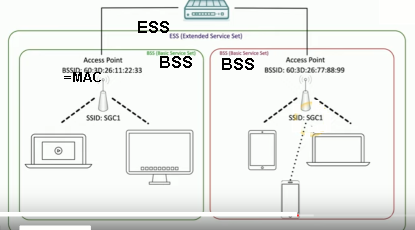
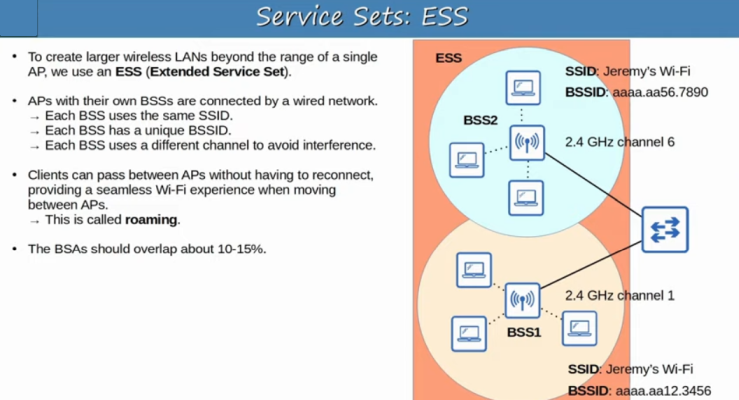
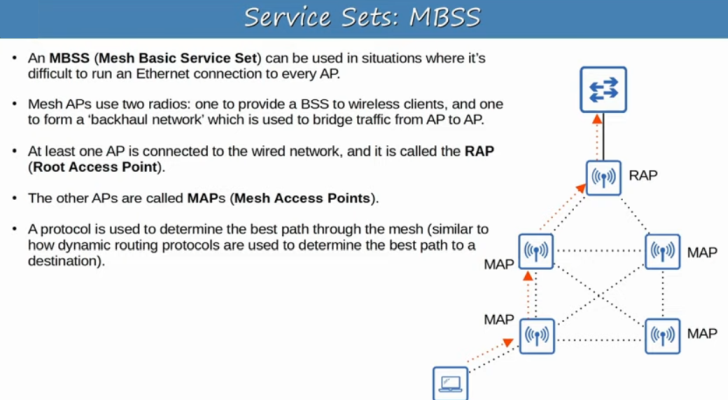
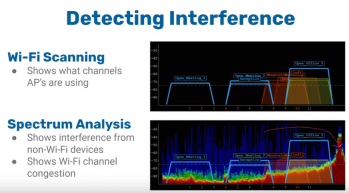
site survey for placement of APs: measure signal strengths.
Microsoft Zeroconf (or WNIC software) scans channels, find SSIDs, connects to strongest or preferred or chosen.
| Standard | Year | Key distribution | Device authentication | User authentication | Encryption | WEP | 1997 | static | yes (weak) | none | yes (weak crackable 40-bit) | Cisco | 2001 | dynamic | yes | yes | yes (TKIP) | WPA | 2003 | both | yes | yes | yes (TKIP) | WPA2 802.11i | 2005+ | both | yes | yes | yes (AES) CCMP | WPA3 | 2018 | yes | yes | yes (AES) CGMP |
|---|
Discourage general users:
SSID cloaking: not sent in beacon (or no beaconing?). (but client with null SSID sends Probes.)
MAC filtering: AP has list of allowable MACs. (but hacker can spoof MAC.)

Guest network can only go to Internet.
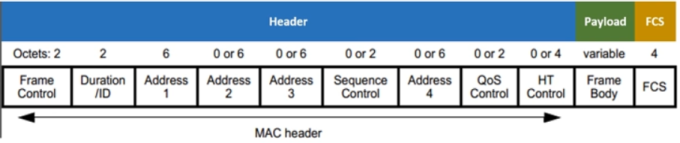
Management and control frames are essentially Layer 2 only.
Management frames between AP and client:
Beacon: broadcast by AP (typically every 100ms), MAC of AP, SSID, supported data rates. Can be turned off.
Client listening on all channels for beacons: passive scanning.
If no beacon detected or doesn't want to wait, can send Probe Request (active scanning)
either to specific SSID or "any". AP can respond with Probe Response unicast with similar info as beacon.
Authentication frames, optionally.
Association Request from client. Response from AP.
Control frames:
ACK 13B contains MAC of intended receiver. Acknowledging successful receipt of previous frame.
WiFi is a reliable network.
n introduced Block-ACK: acknowledge a block of frames received.
RTS and CTS optionally to solve: 1. hidden node problem (manually configured in AP?)
and 2. "protection" in mixed b/g networks
WNIC and/or its driver remove management and control frames and changes data frames
to look like Ethernet frames;
thus Wireshark (on Windows, with most WNICs) doesn't see the raw frames,
only sees "fake" Ethernet frames..